By Josh Kurjan
In almost all cases, security incidents are preceded by distinct and observable patterns of behavior. If identified and managed prior to a biosecurity incident, the risk of such an incident occurring or succeeding can be significantly reduced. It costs far less to prevent an incident than it does to manage the consequences of one, especially with respect to the unauthorized acquisition and release of valuable biological materials.
Life scientists understand that biohazards pose a significant risk to themselves, public and animal health, and the environment. As such, safety in the laboratory environment is a significant concern. Threat actors, a significant factor of biosecurity risk, are generally less understood by those charged with biosafety and biosecurity responsibilities. Threat actors are adversaries with the intent and ability to execute a hostile action impacting biological materials, expertise, equipment, facilities, personnel, technology, and/or intellectual property.
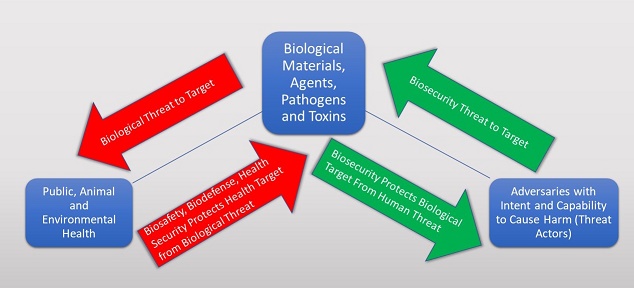
Operationally, not all risks are equally evaluated. Safety risk calculates the likelihood and consequence of relatively stable hazards that are predictable over time. Biosafety risk can be reliably reduced through a hierarchy of controls in a steady state. Security risk, on the other hand, is dynamic and dependent upon instrumental human behaviors. Biosecurity risk reduction efforts must be responsive to real-time changing conditions, over which we have less direct control. Therefore, while biosafety risk assessment can be more accurately predictive, biosecurity threat and risk management approaches must be more preventative in nature.
Life scientists and biosafety professionals, while experts in their fields, often lack operational experience in the security management disciplines underlying biosecurity. This is particularly true when it comes to the assessment and management of threat actor behaviors. Proper threat assessment and management is critical to the application of effective security measures against an intelligent adversary. In almost all cases, security incidents are preceded by distinct and observable patterns of behavior which, if properly identified and managed, could significantly reduce the risk of a biosecurity incident occurring or succeeding. The cost of preventing such an incident is far less than managing the consequences, especially with respect to the unauthorized acquisition and release of valuable biological materials.
Threat actors impacting biosecurity risk can be broadly classified as either “insider” or “outsider” threats. These individuals may target valuable biological materials and related sensitive information for unauthorized acquisition, theft, diversion, misuse or intentional release. They might also target specialized equipment, technology or expertise, or attempt to deny the organization success in executing its mission. Significant variables include motivation, goals and targets, tactics, and levels of access. Whether insider or outsider, all threats must (1) formulate an intent to act; (2) acquire the ability to conduct that action; and (3) exploit opportunity to implement the act itself. These three areas provide a common framework of behavior associated with an outsider’s hostile planning cycle or an insider’s pathway from thought to action.
Fortunately, threat behavior announces itself, telegraphing behaviors detectable by a trained observer. The outsider’s hostile planning cycle typically includes: broad target selection, intelligence and surveillance, specific target selection, pre-attack surveillance and planning, attack rehearsal, actions on the objective, and depending on the mission, escape and exploitation. The insider’s actions, adopted from the targeted violence continuum (Calhoun and Weston, 2003), may include the following stages: grievance (real, perceived or manufactured), ideation, planning, preparation, breach, and implementation. Each of these stages can be categorized into the intent, ability and opportunity framework, and can be proactively mitigated through proper identification, assessment, and management of behaviors of concern.
The opportunity stage occurs at the intersection of a threat actor and their identification of vulnerability in the organization’s security posture. A threat can still be denied or neutralized at this stage, although security countermeasures at this point are reactive rather than proactive, and may be insufficient at stopping an intelligent adversary who has adapted their planning, preparation and tactics to account for such defensive capabilities.
Historically, physical security perimeters have been the most readily identifiable features of any security program and retain value as platforms for delineating enforceable boundaries, and for emplacing technology to detect anomalous behaviors. In the life sciences, the perimeter extends as far as the reach of an institution’s personnel and the Internet, and as deep inside the laboratory suite as the bench upon which they work. Borrowing a concept from the science of cyber security, human behavior transcends the traditional perimeter. Individual accountability and behavior analysis are critical to the detection and reporting behaviors of concern from insider or outsider threats. Biosecurity countermeasure planning must embrace the concept of tuning the “humanware” element of biorisk management.
A considerable weakness of many biosecurity programs I’ve observed is a lack of operational experience directly relevant to threat behavior analysis. In practice, this translates to personnel who do not know what to look for or how to look for it. Integrating a strong pre-employment and pre-access suitability (different from qualification) requirement can provide a robust capability to screen for potential candidates who may pose a security risk. But this is only one step towards building a mechanism for active, continuous and real-time threat behavior identification, assessment, and management. Capacity enhancements through training programs in behavioral aspects of biosecurity can significantly improve security and amplify return on investment. Increasing the sustainability and durability of biosecurity programs through employee contribution promotes individual accountability and an enduring security capability in bioscience institutions where funding and resources are scarce.
If you’d like to comment on this post, please provide comments below. We welcome your thoughts!




Leave a Reply